Design Software
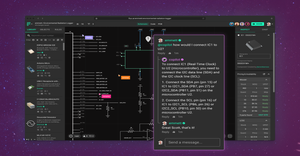
CNC machining 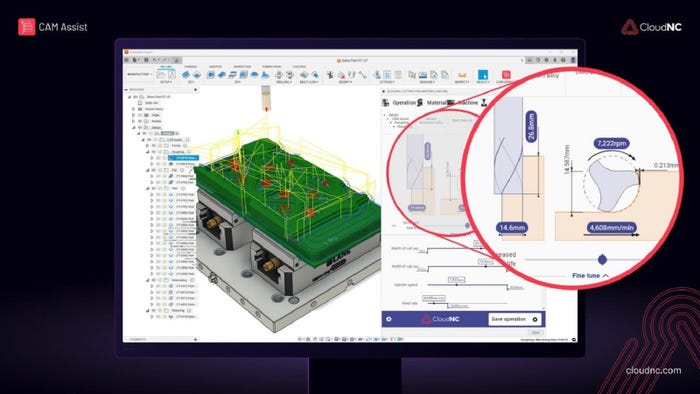
Industry
Catch These New AI Products and SystemsCatch These New AI Products and Systems
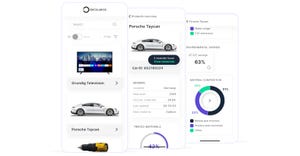
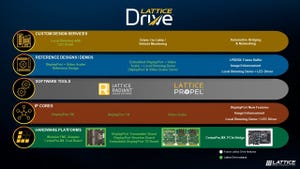
We’re looking at AI visual inspection, AI driven CNC machining, an AI analyzer, and more.
Sign up for the Design News Daily newsletter.