Automotive Engineering
More Topics
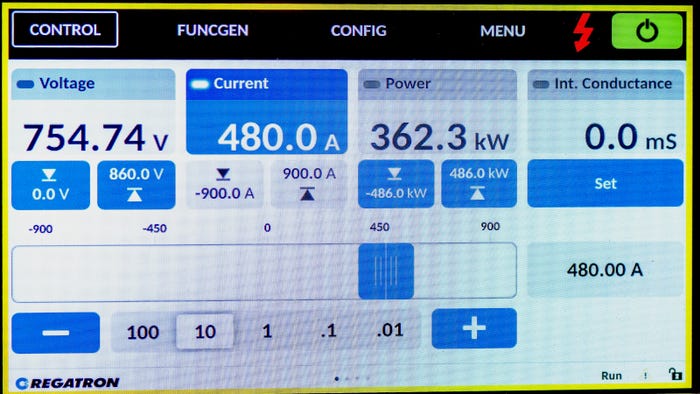
The IIHS performs a pedestrian automatic emergency braking test.
Automotive Engineering
New NHTSA Automatic Braking Rule Could Save 360 Lives a YearNew NHTSA Automatic Braking Rule Could Save 360 Lives a Year
The agency predicts that nighttime pedestrian detection requirements could prevent 24,000 injuries every year.
Sign up for the Design News Daily newsletter.