November 17, 2014
Back in August, reports started emerging of mysterious fake cellphone towers popping up all over the US. It led many to assume that there were actually strange towers of unknown purpose dotting the nation. The truth is these weren't physical towers of any sort, but devices that were being made to trick your cellphone into thinking it was a tower.
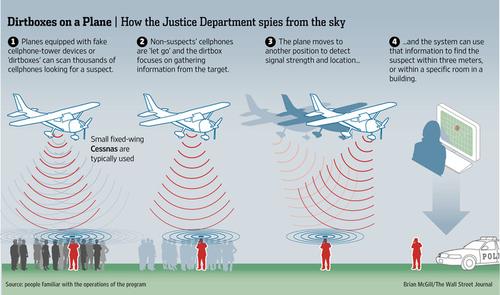
Why would such a thing exist? There haven't been any definitive answers, but the Wall Street Journal has reported that the answer may lie in a 7-year-old US Department of Justice program to track criminals via their cellphone, using devices attached to airplanes. The publication reported that sources wouldn't confirm or discuss specifics about the program but did say these surveillance flights take place on a regular basis. The purpose is to track criminals and fugitives, but doing so requires a sweep that captures a lot of cellphone data from a given area. Once a suspect's phone is found, the device releases the non-suspect phones.
Certainly news like this is going to fuel a lot of speculation. Every time a plane flies overhead does that mean the government is listening to our phone calls? The truth is not nearly that scary, but it does beg a question of just how possible that is, and how did we get to a point where the phones in everyone's pockets can be used to track us.

The fake towers were discovered by people using the Cryptophone. The Cryptophone is an Android-based cellphone, using the Samsung Galaxy S3 as its platform, that provides encrypted messaging and voice over IP communication across any cellular network. It runs on a “hardened' version of the Android OS that GSMK, the company that manufactures the phone, says plugs 468 security vulnerabilities found in typical Android phones. One of the other features of the Cryptophone is the ability to let users know when they may be connecting to a phony cellphone tower.
Les Goldsmith, CEO of ESD America, the company that distributes the Cryptophone, said these vulnerabilities have nothing to do with the brand, model, or even the operating system (OS) of your phone because these fake towers (or “dirtboxes” as they're referred to by some sources) take advantage of an essential function of your phone — the need to communicate with a cellular tower, for a sort of handshake that gives a phone access to a cellular network. “Every cellular phone searches for an available cell tower otherwise you can't make calls or receive data on a network,” Goldsmith said. The way this is done is through a phone's unique International Mobile Subscriber Identity (IMSI) that identifies and verifies a phone as being part of any particular network.
All of this is handled by the phone's baseband processor, the heart of the phone which functions as a middleman between the OS the cell towers. The baseband has been notoriously problematic for security professionals. A 2012 study from the University of Luxembourg showed that hackers can exploit vulnerabilities in a phone's baseband processor to commit a plethora of malicious deeds including accessing the phone's microphone and camera to record audio and video, placing unauthorized calls and texts, and even sending data – all without the owner being aware. In certain models of phones (those running the Qualcomm MSM7200 and similar system-on-a-chip platforms) accessing the baseband will let an attacker bypass any security placed in the phone's OS and take control of the whole device.
Goldsmith said the dirtbox devices are likely some sort of “IMSI catcher” – a device that gathers information from phones by tricking them into connecting to it.“ Think of (the cellular network) like a funnel. Everyone's phone runs through the funnel. And with a filter you can catch the phone you want.” The IMSI catcher is that filter, meaning essentially, you can find the location of the cellphone you're after by sweeping an area.
About the Author(s)
You May Also Like



