Remote and Secure Provisioning Essential in Age of COVID-19
Remote provisioning of network devices is critical for IoT deployment, as well as the support of millions of remote workers, during the COVID-19 crisis. But what about security?
May 12, 2020

A few years back, the rollout of the much touted 50B connected devices for the IoT network was in danger of falling short. The reason for the slowdown in the rollout was not due to the usual suspects of immature technologies, high cost, or market demand. What was slowing the build out of IOT devices – especially gateways and cameras – was a lack of between security to enable scalability.
Without an easy and secure way to deploy and provision IoT system, device manufacturers and cloud-based service providers could not realize the benefits or profits offered by a timely IoT rollout. The selection, deployment and run-time management of software and hardware resources, also known as resource provisioning, has long be a challenge in the networking world.
Fortunately, this problem was addressed with approaches like zero-touch provisioning (ZTP), automated access provisioning (a part of lifecycle management for IoT devices), digital certifications and related techniques.
Zero touch provisioning or onboarding allows devices to be provisioned and configured automatically, eliminating most of the manual labor required to place them on the network. In essence, a device installer plugs the device into the network and flips a switch turn it on and verify its location. After which, remote network administrators could take control of the device. In this way, any number of devices can be provisioned and configured automatically, eliminating most of the manual labor involved with adding them to a network.
The remote provisioning approach worked well for increasing the rollout of IoT networks. The same approach is being used to quickly bring on the millions of remote workers required to work at home thanks to COVID-19.
|
Image Source: Adobe Stock |
Here’s how remote provisioning helped to improve the rollout of the IOT. The challenge was that early IOT devices relied on self-discovery techniques when installed on a network. This approach was easy for the installers but gave IT department’s headaches as the devices would simply appear non-secured on the network. IT departments quickly slowed down the installation of devices by forcing operations departments to secure each device. This immediately improved the security of the devices but put the brakes on the rapid deployment of IOT systems.
IT departments enacted a number of traditional but very time-consuming solutions to ensure each IOT device was secure. To begin with, they required the operations department to stage all IOT installations with pre-imaged devices. While this solution worked great in the past for PCs and laptops with pre-imaged hard drives or network interface cards, it didn’t work well for the enormous number of IOT devices.
The next approach revolved around the operations person contacting IT for a unique key for each and every installation of an IOT device. This manual provisioning was very time consuming and prone to error.
Another idea was to encourage IoT device OEMs and ODMs to pre-configure their IoT devices for specific cloud platform providers. [An ODM is a company that designs or builds a product from another company’s specification.] This way, the provisioning burden could be outsourced to cloud providers. Unfortunately, the large number of cloud providers like Amazon, Microsoft, IBM,Honeywell and others meant that OEMs and ODMs had to validate, document, and track a unique device identification SKUs for each cloud platform.
The eventual solution was to create a platform where any OEMs and ODMs needed to create only a single image for their devices. After manufacturing, the device would become fully provisioned on initial power-up by the installer and ready for handoff to a back-end platform provider for operation.
The idea was to enable a unique identifier for each device during manufacturing, e.g, a semiconductor chip, a PCB or module. To implement this idea, a signed certificate and a public key were created during the manufacturing process. The public key would eventually containe the chain of signature that established device ownership as the device went through the manufacturing and event deployment process. In this way, the ultimate device owner could prove it is the rightful owner of that device. The certificate could then be used to authenticate the device when the device is provisioned in the field.
One drawback of this approach was its reliance on a traditional Public Key Infrastructure (PKI), which gave hackers a way to trace the ownership of the device. The problem was that the previous owners of the device couldn’t remain anonymous while granting access. A given public certificate contained the key owner’s name and information, thus making the ownership of the secured information known to hackers. If the same device was verified multiple times, its activity could be tracked, which would allow hackers to create a threat map from which denial of service attacks could be launched.
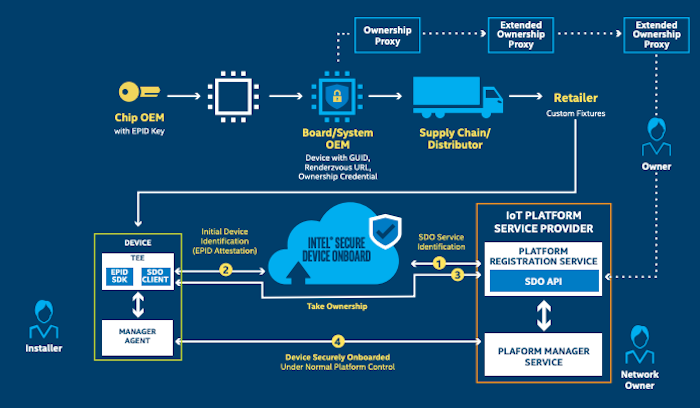
Various remote provisioning platforms handle this shortcoming in different ways. For example, Intel Secure Device On-boarding (SDO) platform uses its own Enhanced Privacy ID (EPID) technology that establishes anonymous secure channels where endpoint authentication is hidden, unlike traditional public key methods. Also EPID collects no identity data but instead uses approved levels of access and not any personal information like a network MAC-ID or who they are.
Another approach is to use PKI technology with a Trusted Platform Module (TPM) for secure
key storage. To help OEMs and ODMs implement both PKI and TPM, Sectigo and Infineon have joined forces. Sectigo provides an automated PKI management system to secure websites, connected devices, applications, and digital identities. Infineon, well-known for its semiconductor chips, offers a Security Partner Network to secure devices during the manufacturing process.
Remote and secure provisioning of network devices is critical for the rollout of IoT as well as the addition of hundreds of thousands of new devices to support a remote workplace during the COVID-19 crisis. Several electronics and software firms such as Intel, Infineon and Sectigo – among others) have stepped up to handle this challenge.
|
Image Source: Intel Secure Device OnBoarding (SDO) |
John Blyler is a Design News senior editor, covering the electronics and advanced manufacturing spaces. With a BS in Engineering Physics and an MS in Electrical Engineering, he has years of hardware-software-network systems experience as an editor and engineer within the advanced manufacturing, IoT and semiconductor industries. John has co-authored books related to system engineering and electronics for IEEE, Wiley, and Elsevier.
About the Author(s)
You May Also Like