How Best Can IT Departments Battle Attacks From Anonymous Quantum Computers?
What will be quantum computing’s impact on cybersecurity? Can certificates avoid an apocalypse?
June 28, 2021

Quantum computing is a special topic area in quantum information science. A traditional computer has two states, on and off, while a quantum computer can also use a third state known as a superposition. This gives a quantum computer very unique capabilities, such as solving integer factorization very quickly. A traditional binary computer solves that particular mathematical problem slowly, whereas a quantum computer with an efficient algorithm can solve that same problem much more quickly. For example, in breaking RSA-2048, the time could be reduced from trillions of years to possibly just minutes.
Traditional computers measure their data in bits, but quantum computers utilize a ‘quantum bit’ or qubit. The main challenge for quantum computing is to keep qubits stable, which is a very important area of ongoing research and a requirement for the commercialization of quantum computers. As researchers build quantum computers with larger numbers of stable cubits, they can solve these difficult mathematical problems much more quickly.
The security of RSA encryption, one of today’s main cryptographic algorithms, is based on the computational difficulty of factoring large integers into prime numbers. The security of Elliptic Curve Cryptography (ECC), the main alternative for RSA, is based on the difficulty in finding the discrete logarithm of a random elliptic curve element. These two algorithms form the foundation for most PKI implementation, which, in turn, provide the security for most data protection and secure communication solutions in use today.
ECC and RSA encryption can be performed quickly by traditional computers, but traditional computers would require many years to break these encryption schemes. For example, for RSA-2048, current computers require roughly 300 trillion years to break the encryption. Quantum computers change this.
Once quantum computers reach the point that enough stable qubits are attained, they will be able to solve the math problems underlying these algorithms and thereby break the encryption schemes in a matter of weeks, days, or even minutes. For RSA encryption, this is done using Shor’s Algorithm. To maintain the security of data, new cryptographic algorithms must be implemented. Currently, industry organizations, researchers, and leading security companies are developing new cryptographic algorithms that are resistant to quantum computing in general and to Shor’s Algorithm in particular.
The goal of these new algorithms is to ensure that they will be available to secure information and communications before the current cryptographic algorithms are broken. However, while quantum computers are massively faster at solving many mathematical problems, they are not simply universally faster at all processing tasks and offer an advantage only for a limited set of mathematical problems. By using different mathematical approaches, it is possible to develop cryptographic algorithms that can be efficiently executed on traditional computers but that are resistant to attacks from quantum computers.
Basically, the solution is a combination of new math alongside new PKI tools. Thankfully, some of the best minds on the topic have already been researching the most optimal quantum-resistant algorithms from a security and performance standpoint.
What is the quantum apocalypse?
The inevitable day when quantum computing renders RSA and ECC encryption algorithms obsolete could be so crippling to society that the security sector has deemed it the “Quantum Cryptographic Apocalypse.” The hype isn’t unfounded. RSA and ECC encryption are used to secure every data source and system across industries: factories, data farms, utilities, e-commerce and banking systems, transportation, communication networks, and much more.
When enough stable qubits are attained in a quantum computer, the current cryptographic algorithms will be rendered insecure. That point in time is known as the ‘quantum apocalypse.’ While it will take time to get there, experts estimate that the date is only 6-10 years away.
There has been a great deal of research to find the next generation of quantum-resistant algorithms, as well as standards development on PKI certificates, that can act as an operational bridge between the current generation of algorithms and post-quantum resistant algorithms. In July 2020, the National Institute of Standards and Technology (NIST) announced the third-round candidates consisting of 7 finalists and eight alternate algorithms.
While quantum computing is still in the development phase, the Quantum Apocalypse is coming.
Sound scary? Well, it can be. If you have information, systems, and devices that need to be kept secure and private for years and decades to come, your organization needs to prepare now.
Yes, quantum computers are complex and expensive systems that, at first, will only be affordable for major international technology organizations. However, their use can then spread to various nation-states and eventually to cybercriminals and hackers.
The good news is that there are steps that the manufacturing and tech industries can take now.
Phased Migration to Quantum-Safe Cryptography
Migrating to quantum-safe crypto algorithms will require planning and updates to multiple systems. All need to be protected. A company’s internal data management and communications systems, as well as third-party applications, servers, and systems, will all need to be updated.
Engineers and development teams must begin planning now to migrate to quantum-safe crypto. For factories and large enterprises, these measures will be a major undertaking.
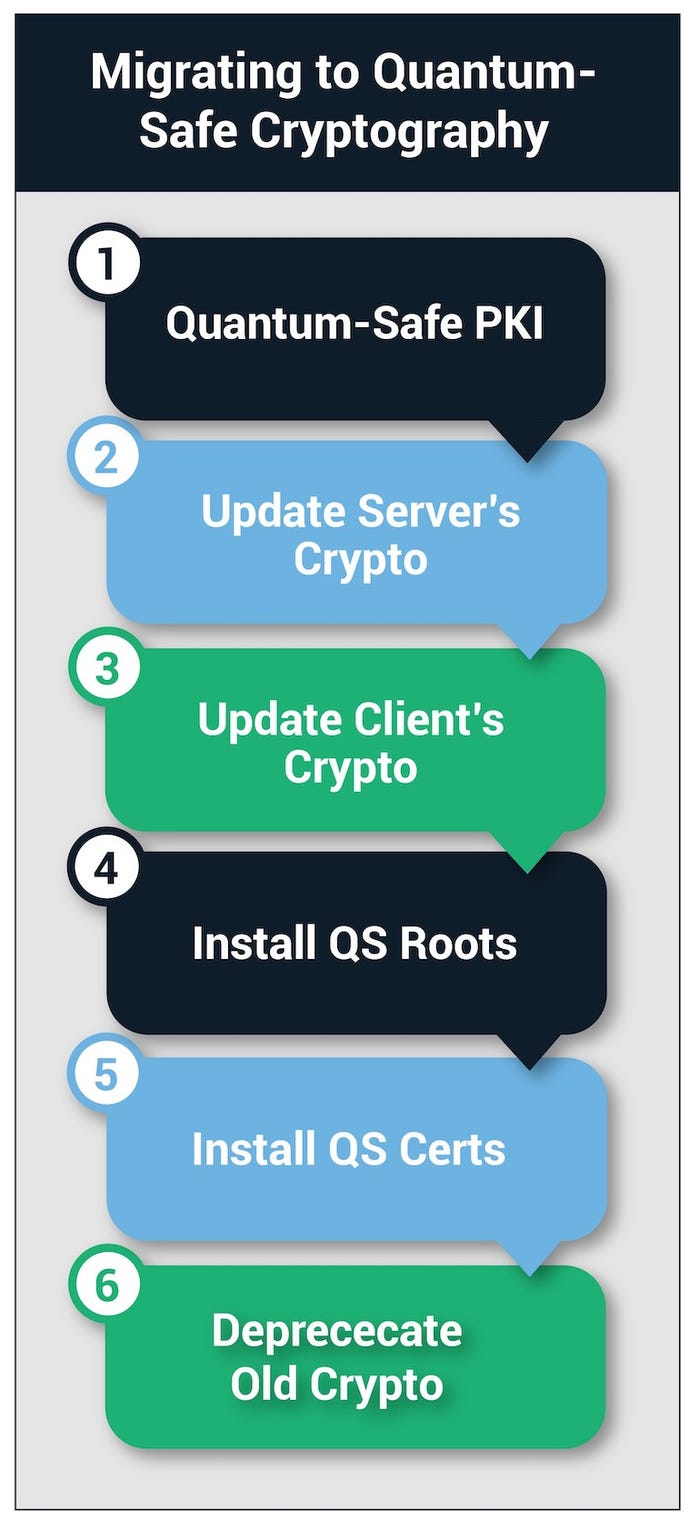
The following six steps are required for either direct or hybrid migration plans.
Upgrade to a quantum-safe PKI security infrastructure
The first step towards migrating to quantum-safe cryptography is to upgrade the PKI infrastructure, including the certificate authority, with support for quantum-safe crypto algorithms. Rather than trying to upgrade internal PKI systems, this may be an ideal time for companies to migrate to a commercial Certificate Authority (CA), such as Sectigo, which can provide commercial support for quantum-safe crypto algorithms.
Whether moving to an in-house PKI system or adapting a solution from a commercial vendor, it is critical that the CA provide support for quantum-safe crypto algorithms and quantum-safe certificate issuance. If the IT security team chooses to use hybrid certificates, they must select a CA that supports both hybrid certificates and pure quantum-safe certificates.
Hybrid certificates contain both a traditional ECC or RSA key and signature and a new quantum-safe key and signature. This allows systems that have been upgraded to support quantum-safe algorithms to use the newer algorithms, while older systems can still use the certificate by utilizing the traditional algorithm. This can also allow interoperability of older and newer systems during the migration period.
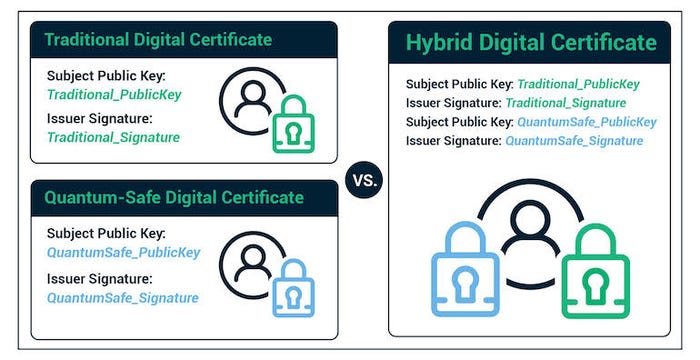
Once an organization upgrades its existing CA or selects a new CA, the CA must issue a new quantum-safe root and intermediate certificate.
Update server applications to recognize and use new crypto algorithms.
Migrating to quantum-safe crypto requires updating the crypto libraries used by server applications to support both the new crypto algorithms and the new quantum-safe certificate formats, including hybrid certificates if used. If hybrid certificates are used, server applications will need to recognize and process both traditional RSA/ECC certs and hybrid certs containing quantum-safe crypto keys. This requires the server applications to distinguish between the two different certificate types and handle each with the proper crypto algorithm for that certificate type.
Update the client crypto algorithms.
IT and development teams will also need to update a wide range of client applications to use quantum-safe crypto algorithms. Once fully and safely upgraded, administrators can discontinue the use of traditional RSA/ECC keys/certificates in client applications and instead use the new quantum-safe equivalents.
The exception to this policy is a client application that communicates with multiple server applications that may not all be simultaneously upgraded to quantum-safe crypto. In this case, hybrid certificates will allow the client to work with servers supporting traditional RSA/ECC crypto while at the same time, use quantum-safe algorithms with servers that support these newer algorithms.
Install quantum-safe roots on all systems.
Each security system utilizing PKI has a trusted root store. This root store contains the certificates for the root and intermediate CAs that issue certificates within the PKI system. Once systems have been updated to support quantum-safe crypto algorithms, these root stores must also be updated to add the new root and intermediate certificates.
All connected devices/applications will need quantum-safe certificates.
After IT teams have updated all a company’s systems to support quantum-safe crypto, they must issue new certificates and install them on all the endpoints. Once completed, each device can begin using quantum-safe crypto algorithms, as enabled by the new certificates.
The Final Step – Get rid of the old.
The final step in migrating to quantum-safe crypto is to deprecate the traditional encryption algorithms, so they are no longer used. This can be done gradually on applications and systems as they are migrated to the new algorithms. After all, systems have been migrated, the root ECC and RSA certificates should be revoked, ensuring they are not used by any systems.
Summary
Quantum computers capable of breaking traditional crypto algorithms will arrive within the next decade. Yes, at first, they will be limited to big international companies and nation-states, but eventually, quantum computing will be affordable for the average cybercriminal and hacker.
For most organizations, the task of migrating to new, quantum-safe crypto algorithms will require a major, well-planned effort spanning a variety of internal development teams and third-party vendors. Companies will have to upgrade the PKI systems that they are using along with the company-wide applications using these certificates.
Hybrid certificates enable a safe, gradual migration of systems, but ultimately all systems using ECC or RSA encryption must migrate to new, quantum safe-crypto algorithms. Otherwise, an organization’s applications and systems will be vulnerable to attacks using quantum computers.
Alan Grau has 30 years of experience in telecommunications and the embedded software marketplace. He is VP of IoT at Sectigo, the world’s largest commercial Certificate Authority and provider of purpose-built, automated PKI solutions. Prior to founding Icon Labs, Alan worked for AT&T Bell Labs and Motorola. He has an MS in computer science from Northwestern University.
About the Author(s)
You May Also Like



