Why Are Embedded Industrial Control Devices Now Vulnerable To TCP/IP Attacks?
Critical flaws found in embedded TCP/IP stacks may widely affect industrial control devices.
September 22, 2021
Cybersecurity experts have found numerous vulnerabilities affecting a commonly used TCP/IP protocol network stack used in millions of Operational Technology (OT) devices. In contrast to IT systems – which manage data - OT devices control the physical world, especially in the industrial and manufacturing spaces.
Further, the affected OT devices are manufactured by hundreds of vendors and deployed in manufacturing plants, power generation, water treatment, and infrastructure sectors. For the most part, the OT devices are part of the industrial IoT marketplaces, all of which are highly susceptible to attacks and flaws that result from issues within the TCP/IP network communications architecture.
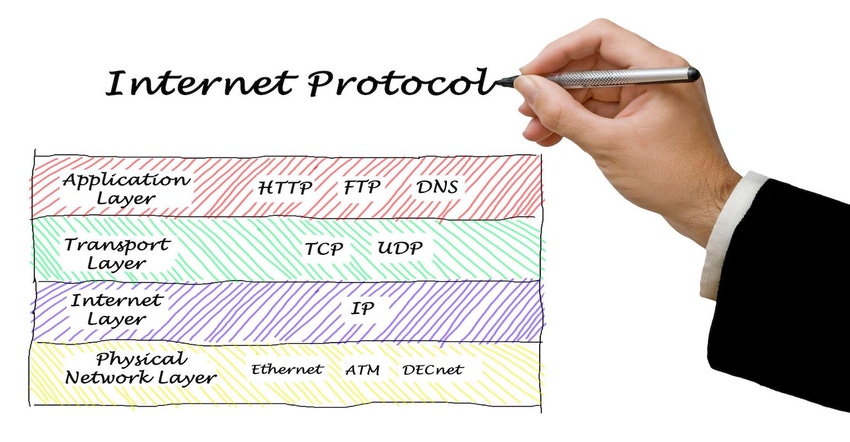
Since its inception, the TCP/IP network protocol stacks have formed the backbone of the Internet. Smaller, tailored versions of the full-up Internet stack were created decades ago for embedded systems later used in connected IIoT devices. The embedded TCP/IP stacks – sometimes called NicheStack - combine applications, transport, network, and physical components.
NicheStack is a closed source IPv4 network layer and application implementation for operating systems. It is one of three available from InterNiche Technologies, Inc., designed for use in embedded systems.
Researchers have identified more than a dozen vulnerabilities in the NicheStack TCP/IP stack used by many OT vendors. The vulnerabilities are collectively tracked as INFRA:HALT, which targets NicheStack, potentially enabling an attacker to achieve remote code execution, denial of service (DNS), information leak, TCP spoofing, and even DNS cache corruption.
TCP/IP Attack
How might an attack be carried out? One possible scenario would involve an external attacker using an internet-exposed device running NicheStack to infiltrate the targeted network. The theoretical attack was suggested by researchers from Forescout Research Labs and JFrog Security Research, who initially discovered the security holes,
In such a scenario, the attacker uses one critical INFRA:HALT vulnerabilities to send specially crafted Denial of Service (DNS) requests. The malicious DNS request contains a shellcode that instructs the first device to send a malicious FTP packet to a second device on the manufacturing network — i.e., a programmable logic controller (PLC) on a factory floor —to cause it to crash. The PLC crash causes the disruption of the physical process associated with the controller.
This is not the first time researchers have identified potentially severe vulnerabilities in TCP/IP stacks. Previously discovered issues include AMNESIA:33, NAME:WRECK, and NUMBER:JACK.
John Blyler is a Design News senior editor, covering the electronics and advanced manufacturing spaces. With a BS in Engineering Physics and an MS in Electrical Engineering, he has years of hardware-software-network systems experience as an editor and engineer within the advanced manufacturing, IoT and semiconductor industries. John has co-authored books related to system engineering and electronics for IEEE, Wiley, and Elsevier.
About the Author(s)
You May Also Like





