Manufacturing Becomes the Biggest Cyber Attack Target
While cyber attacks on networks at Sony, Target, and the US Government are getting all the press, the greatest cyber vulnerability is in manufacturing.
January 11, 2016
While cyber attacks on networks at Sony, Target, and the US Government are getting all the press, the greatest cyber vulnerability is in manufacturing. “By raw numbers, and by the numerous manners of attacks, manufacturing is the most targeted area now, even compared to financial services,” Chet Namboodri, senior director of Global Private Sector Industries at Cisco, told Design News. “Financial services gets more press, but industrial networks get more attacks.”
Rockwell Automation and Cisco have been working together for years to create practices that protect industry against cyber threats. Industrial Automation and Control System (IACS) networks are generally open by default. The openness supports technology coexistence and device interoperability.
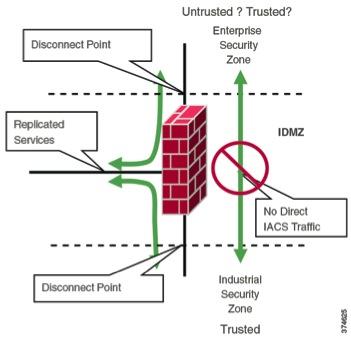
Using high-level IDMZ design principles, all IACS network traffic from either side of the IDMZ terminates in the IDMZ, with no IACS traffic that directly traverses the IDMZ.
(Source: Cisco and Rockwell)
That openness also allows for vital data exchange between plant operations and the organization’s enterprise system. Yet openness also requires that IACS networks be secured by configuration and architecture to defend the perimeter as well as defending the system internally. Many organizations and standards bodies recommend segmenting business system networks from plant-wide networks by using an Industrial Demilitarized Zone (IDMZ).
The vulnerabilities of a connected plant have been around for years, long before attacks became commonplace. Rockwell and Cisco joined forces nearly a decade ago to address the problem. “We have been working with Rockwell for eight years to develop an architecture for the manufacturing space,” said Namboodri. “Our primary intent is to lock down security beyond just network security, and to take security down to the device and application level. The latest in our IDMZ security product introductions have been in that area.”
According to Rockwell and Cisco, there are specific principles that go into creating a successful cyber security IDMZ:
No direct path between the Industrial and Enterprise Zones
No common protocols in each logical firewall
EtherNet/IP IACS traffic does not enter the IDMZ; it remains within the Industrial Zone
Primary services are not permanently stored in the IDMZ
All data is transient; the IDMZ will not permanently store data
Set-up functional sub-zones within the IDMZ to segment access to IACS data and network services (for example, IT, Operations and Trusted Partner zone)
A properly designed IDMZ will support the capability of being unplugged if compromised,while still allowing the Industrial Zone to operate without disruption
READ MORE ARTICLES ON CYBER SECURITY:
For decades, the plant network stood apart from the rest of the enterprise. Yet the advantages of extended networks, connections to the enterprise system, and device connectivity were profound. The benefits include increased uptime and decreased downtime -– too much to ignore. “Years ago our customers left their control system unconnected. But the increasing demand for information drives connectivity. We saw increased risk, so we needed to leverage some well-known skills that could make it manageable,” Tony Baker security leader at Rockwell Automation, told us. “We leverage some of Cisco’s key technology to bring it to the manufacturing space. We brought security together with Cisco so our customers can continue to share information.”
Part of the strategy in creating successful security is to accept the fact that it’s a continually growing challenge. “Even in the last year attacks have become more sophisticated and more frequent, but we can expect that year after year,” said Baker. “As technology expands, we’re going to see more and more risk. This is not a static state, so you need to have the people in place, and you have to continue to enhance your protection all the time.”
Rob Spiegel has covered automation and control for 15 years, 12 of them for Design News. Other topics he has covered include supply chain technology, alternative energy, and cyber security. For 10 years he was owner and publisher of the food magazine Chile Pepper.
Like reading Design News? Then have our content delivered to your inbox every day by registering with DesignNews.com and signing up for Design News Daily plus our other e-newsletters. Register here!

Design engineers and professionals, the West Coast’s most important design, innovation, and manufacturing event, Pacific Design & Manufacturing, is taking place in Anaheim, Feb. 9-11, 2016. A Design News event, Pacific Design & Manufacturing is your chance to meet qualified suppliers, get hands-on access to the latest technologies, be informed from a world-class conference program, and expand your network. (You might even meet a Design News editor.) Learn more about Pacific Design & Manufacturing here.
About the Author(s)
You May Also Like


.jpg?width=300&auto=webp&quality=80&disable=upscale)


