The Hubble space telescope in orbit.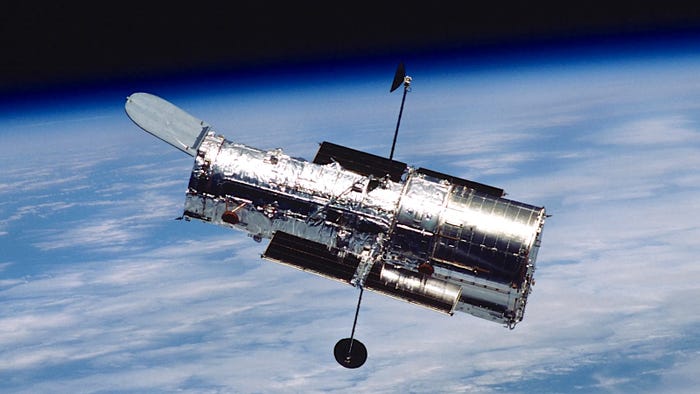
Industry
Video: NASA Goddard's 40 Years of Non-Stop Hubble OperationsVideo: NASA Goddard's 40 Years of Non-Stop Hubble Operations
NASA's Goddard Spaceflight Center opened its control center 40 years ago.
Sign up for the Design News Daily newsletter.













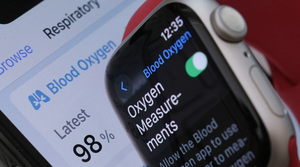















.jpg?width=300&auto=webp&quality=80&disable=upscale)






