Manufacturing Is More Vulnerable to Cyber Attack as IoT Proliferates
The GMSA in Europe has release cybersecurity guidelines to help protect manufacturing from attack.
April 12, 2016
In the rush to deploy IoT devices, an overwhelming number of companies are overlooking security issues. A recent AT&T cybersecurity survey of more than 5,000 enterprises found 85% of respondents are in the process of or are planning to deploy IoT devices. That’s not a surprising percentage given the widespread interest in everything connected. However, only 10% of respondents indicated they feel confident they can secure those devices against hackers.
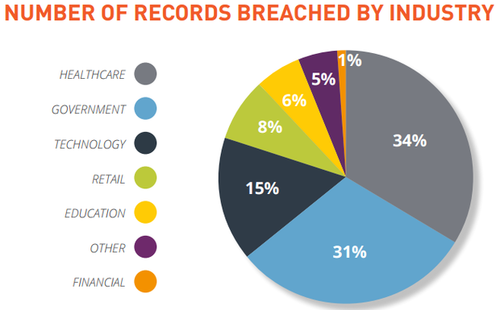
This chart show which industries are getting hit hardest by cyber attacks.
(Source: Gemalto)
To address uncertainty and growing concerns over cyber attacks, the GSMA –- a European standards organization –- has published an IoT Security Guidelines document to help service providers and OEMs better understand cybersecurity threats. The document includes details on the technologies needed to mitigate cybersecurity risk, particularly in manufacturing.
The digital security firm, Gemalto, worked with the GSMA and other industry leaders to establish these new security guidelines and best practices. “Security has never been so important as it is in manufacturing now. If you look at the past four or five years, manufacturing has changed. The manufacturing process is now intelligent,” Jason Hart, CTO of Cloud Solutions and Data Protection for Gemalto told Design News.
Major companies involved in manufacturing such as Rockwell Automationand Cisco Systemshave recently noted that manufacturing is becoming a larger target for cyber attacks. The connected or “smart” factory is becoming increasingly vulnerable. “With the IoT in modern manufacturing, you have connected sensors, and that provides corrective processes,” Hart told us. “The objective is to make the manufacturing process more efficient with less human intervention, with sensors talking to other sensors and making corrections without human interactive.”
READ MORE ARTICLES ON CYBERSECURITY:
The connectivity runs from machine-to-machine points as well as factory-to-enterprise pipelines. That results in multiple entry points. “If I put my bad-guy hat on, there are many points of entry to compromise the manufacturing process. You have sensors, motors, and computers. The point of entry has gone from one to many,” said Hart. “The bad guy knows the attack surface is massive. So security is fundamental. You have to make sure sensor A can’t talk to Sensor B without authentication.”
With all of the machine-to-machine connectivity that IoT offers, security needs to be embedded in the manufacturing process itself. Perimeters around the plant are not sufficient protection any longer. “The manufacturing process hasn’t changed dramatically. You just have more sensors, more inputs, and more outputs,” said Hart. “Security control is simple. You need the process to be highly authenticated down into the chips and the data levels.”
The Attacker Hiding in the System
One of the dangers in today’s cyber attack is the possibility that the breach will not be apparent. An attacker can hide in the network and infect the individual products themselves. “In the event of a breech, it’s going to be the integrity of the data that will be the issue. The attack may not appear until the manufacturing process is finished and the consumer starts buying the product,” said Hart.
He said he expects we will see an increase in quiet breaches that lay low for an extended period before the attack itself. “In the coming years we’ll see fundamental integrity attacks against manufacturing. We may not know its attacked. From a manufacturing point of view the risk is greater,” said Hart. “There’s the potential for physical harm if its manufactured incorrectly, and from a business point of view, it’s the business reputation. Not only do you have integrity, you have the physical element, as well.”
Rob Spiegel has covered automation and control for 15 years, 12 of them for Design News. Other topics he has covered include supply chain technology, alternative energy, and cyber security. For 10 years he was owner and publisher of the food magazine Chile Pepper.
About the Author(s)
You May Also Like


.jpg?width=300&auto=webp&quality=80&disable=upscale)


