Demilitarized Zones Join Defense-in-Depth in Plant Cyber Security Measures
October 21, 2015

With Converged Plantwide Ethernet (CPwE) networks taking center stage and Internet of Things (IoT) initiatives potentially exposing even greater access to networks, securing plant and enterprise networks has become an enduring focus for which there are no absolute solutions.
Given the reality of successful and constant cyberattacks in the news, the best response is still combining layers of security using holistic, defense-in-depth measures that harden both the network configuration and architecture. But there is almost equal attention on the human equation and developing both technology solutions and procedures for properly authenticating and authorizing all types of user access at the network edge.
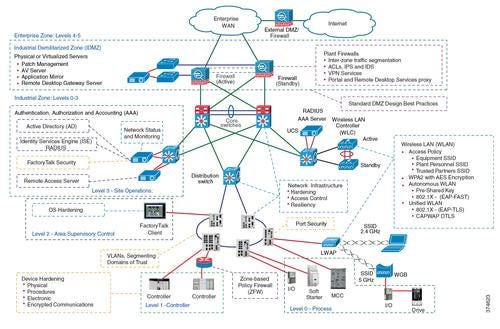
Open by Default
One of the biggest challenges for customers, in addition to breaking away from the old air gap mentality -- that security can be achieved by obscurity -- is wrestling with the fundamentals of how to securely connect applications and machines in the plant. "When it comes to industrial networks, they have generally been open by default. The reason for that is manufacturers want to have coexisting technologies and device interoperability, so they can choose best-in-class products from vendors," Gregory Wilcox, global business development manager of networks at CCNA Routing & Switching for Rockwell Automation, told Design News.
"When a technology or network is open by default, there is a need to secure it both by configuration and architecture. A good architecture provides a strong network infrastructure to defend the edge, using an electronic perimeter to protect network assets. This is where the concept of an industrial demilitarized zone (IDMZ) comes into play, along with configuration tools that enable hardening of the infrastructure through a holistic, defense-in-depth approach," he added.
Wilcox said that, when it comes to a defense-in-depth approach, no single product, technology, or methodology can fully secure an industrial network. There is a requirement for multiple layers of defense-in-depth to combat both internal and external threats, which can also be physical, procedural, or electronic.
Everything done to secure a converged plant utilizing Ethernet means that security is a primary objective and not an afterthought. And while security has always been a core responsibility, now there needs to be more focus on deploying defense-in-depth strategies to defend applications and on making continuous, incremental improvements.
MORE FROM DESIGN NEWS: The Anatomy of a Cyber Security Assessment
Better Identity Services
One important concept being utilized to implement a converged network with Ethernet is identity services. When you think about BYOD, or "'bring your own device," the industrial automation market has been doing this for years. Every subcontractor, integrator, or machine OEM has wanted to be able to plug in a notebook computer to support end-customer machines. Now with machines integrated together into a plant-wide architecture and connected enterprise, there is a need to secure these connections through better management.
"What we are using is the Cisco Identity Services Engine (ISE), which allows authentication and authorization of users at the edge of the network," Wilcox said. "An example is, if a person plugs into a port on an industrial Ethernet switch, we use standard IEEE 802.1X for authentication and go up to the identity services engine and ask, 'Who are you?' An employee can input their credentials to establish what they are authorized to do and gain access to everything they need to do their job."
Whether they are employees or visiting engineers from machinery OEMs, users can be authenticated and granted access to only specific machines and applications. Configuration information can be downloaded from the network to tunnel the user exactly to the network location(s) they need to access, providing flexibility and security from an infrastructure standpoint that works with either wired or wireless networks.
"The identity services engine also provides for self-registration," Wilcox said. "The IT department, whether it is corporate IT or outsourced IT, can set up the system so that plant personnel can register a contractor visiting for the day. Once the contractor signs in, it can download an access control list which allows access to specific resources while denying access to other areas. The system makes this possible without the need for IT personnel onsite."
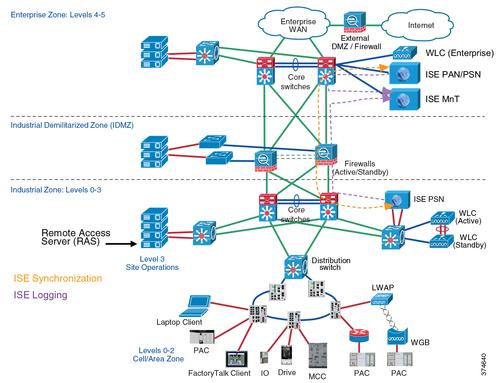
Traversing Plant-Wide Networks
The industrial demilitarized zone provides tools that enable users to securely traverse data across a plant-wide network. Look at some of the industrial security control standards such as IEC 62443 (formerly ISA99) or other standards that the Department of Homeland Security or Idaho National Laboratory provides from a security standpoint. One of the best practices they have deployed, in addition to defense-in-depth, is a demilitarized zone.
About the Author(s)
You May Also Like



