Cyber attacks are taking a new form, with hackers going into a network and exploring for extended periods of time.
April 1, 2016
As companies move more and more of their assets and communications into the cloud, the issue of security keeps coming up. Cloud companies insist their services are secure, noting that their expertise in cyber security can’t be matched by their customers’ in-house servers. Skeptics argue that the cloud is more vulnerable simply because of its broad surface for potential attack. You can see the cloud public position, while you may not be aware of an in-house server.
Cloud security company Alert Logic recently commissioned a study by Forrester Consulting that revealed that IT professionals cite the lack of visibility into their network and aging firewall systems as the top two factors in cyber security vulnerabilities. Thirty-seven percent of respondents estimate that their firm’s sensitive data had been breached in the past 12 months.
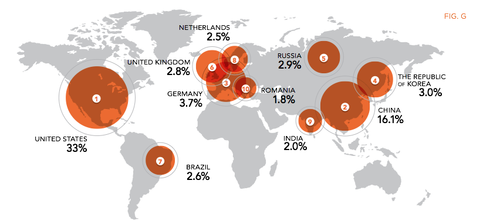
This map shows the sources of cyber attacks in recent history. Perhaps the most surprising aspect of the map is the large percentage of attacks coming from within the US.
(Source: Alert Logic)
Through its work with Forrester and its own annual analytical reports on cloud vulnerabilities, Alert Logic has tracked growing cloud vulnerabilities. “We continue to see an increase in attack frequency for organizations with infrastructure in the cloud. This is not surprising, since production workloads, applications, and valuable data are shifting to cloud environments, and thus so are attacks,” Rahul Bakshi senior director of product at Alert Logic, told Design News.
Meet the New Hacker
The nature of cyber attacks has changed. In the past, major threats came from recreational hackers and disgruntled former employees. Now there is an underclass of hackers who intrude for profit, seeking personal information and trade secrets. “Today’s attackers are a sophisticated lot, using advanced techniques to infiltrate a business environment,” said Bakshi. “Unlike in the past when hackers primarily worked alone using smash-grab techniques, today’s attackers work in groups, each member bringing his or her own expertise to the team.”
READ MORE ABOUT CYBER SECURITY AND HACKERS:
Cyber attacks are now different in nature. Instead of the quick in-and-out, hackers will enter a network and set up shop. “Once they get a foothold, you can see the damage for months. Once they intrude a server or on a network, they start looking around carefully and cautiously, exploring the things they are looking for,” said Bakshi.
Once hackers get into a network, they may sit quietly until they see sufficient reason to begin taking data or doing damage. Security’s goal is to find the hacker before the theft occurs and the damage is done. “Post compromise, they spread and explore. You have to look at the chains, what Lockheed Martin calls the cyber kills chain,” said Bakshi. “Detecting the attack and ascertaining what is going on.”
Rob Spiegel has covered automation and control for 15 years, 12 of them for Design News. Other topics he has covered include supply chain technology, alternative energy, and cyber security. For 10 years he was owner and publisher of the food magazine Chile Pepper.
About the Author(s)
You May Also Like





