Recent attacks point to the need for enhanced IoT security. Will governments help or hinder?
June 23, 2021

With all the ongoing ransomware and cyber-attacks, connected IoT devices need an extra layer of security. New legislation in both Europe and the US are mandating such strengthened security. But what tools are available for embedded IoT engineers to meet these new requirements?
To learn more about providing enhanced protection of connected devices, Design News reached out to Haydn Povey, CEO of Secure Thingz and General Manager for the division Embedded Security Solutions at IAR Systems. What follows is a portion of that discussion.
Design News: Why do connected IoT devices need enhanced protection?
Haydn Povey: The requirements of new legislation for security in IoT devices are impacting us now. With the advent of EN 303 645 and the US IoT, Cyber Security Act signed into law last year, there is now mounting pressure on the Consumer IoT market to meet security standards. However, this is not just limited to Consumer IoT, with regulations evolving quickly in other markets, such as the IEC 62443 requirement for Industrial IoT (Industry 4.0) and similar requirements in medical and automotive.
Design News: Has there been a recent breach that you might reference?
Haydn Povey: The unfortunate reality is that there are many “bad actors” in the real world looking to attack devices. Some of this may be for direct device ransomware, some to build up data to attack individuals' bank accounts, and some may even be nation-state-sponsored attacks on critical national infrastructure. There are several examples here, stretching back to the Mirai Botnet back in 2016.
For example, IoT devices were used to launch a distributed denial-of-service attack, leading to significant outages across the internet. While this was not an attack on the user, per se, it had a major impact on our collective infrastructure. Other specific compromised have included medical devices including pacemakers and intravenous drug dispensers; children’s consumer IoT devices including toys and watches, such as the Safe-KID-one; home security devices including camera systems; and industrial control systems in critical national infrastructure, such as water treatment.
The unfortunate reality is the list is already too long to pull out unique breaches – they happen every day, and it is just the consequences that we are starting to notice. Recently, Forbes highlighted that the chartered ship, Wakashio, spilling oil off Mauritius, is suspected of being hacked. Still, whether this was an IT, OT, or IoT hack is subject to speculation.
Design News: Is the European Consumer IoT Security Standard EN 303 645 similar to the US Cybersecurity Improvement Act?
Haydn Povey: EN 303 645 is very similar to the US Cybersecurity Improvement Act, and both can trace their roots back to the work the IoT Security Foundation undertook back in 2016. The IoT Security Foundation is a successful industry forum that grew out of the need to identify existing “best practices” for security and how this should be applied to emerging IoT challenges.
The EN 303 645 standards is focused around 13 specific requirements, shown in the diagram below, but has three core tenants, these being
No Default Passwords: Ensuring that devices deliver identity and system authentication based on modern cryptographic best practice
Vulnerability Disclosure: Ensuring that organizations must openly communicate how long devices will be supported with updates, have a mechanism to work with security researchers, and communicate to end-users when issues are identified.
Keep Software Updated: Ensuring that devices that have been compromised must be easily patched and updated, presuming that end users are not technical experts.
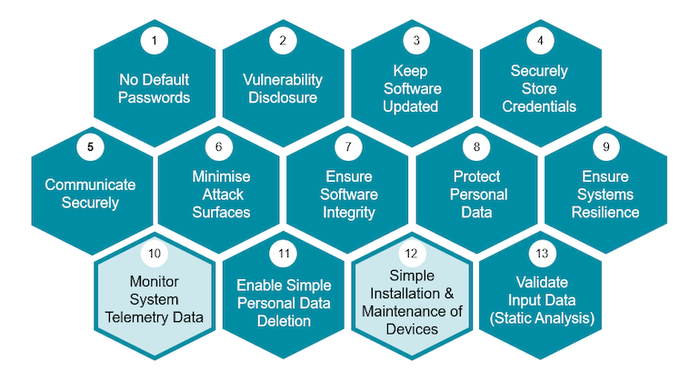
These requirements operate as “good hygiene,” which most modern applications should already achieve. Unfortunately, the reality is different with recent UK government research identifying that only 4% of connected devices achieving sufficient security.
Design News: Are these standards helpful?
Haydn Povey: When we look at compliance with these regulations and the equivalent US ones, it is crucial to demonstrate a clear engineering methodology, ensuring that sufficient thought and effort has been applied to each domain. For example, it is clear that modern cryptographic identity and authentication must be implemented with no default passwords. This must be supported across development and production to ensure every device is unique going out of the factory door.
As we look at other requirements, such as minimizing attack surfaces, secure communications, and securely storing credentials, it becomes obvious that devices must be locked down firmly, ensuring rogue code cannot be injected or operated. Where possible, secure enclaves and advanced security technology, such as the PUF, are properly implemented.
Design News: What supply chain tools will help with enhanced IoT security?
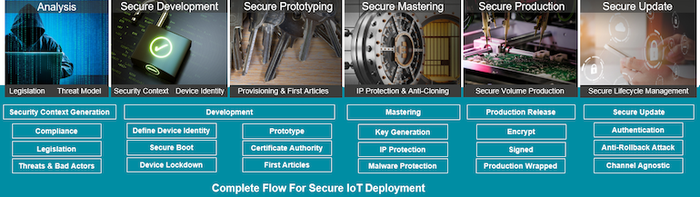
Haydn Povey: The secure supply chain is complex and impacts the traditional design flow in many ways. At Secure Thingz/IAR Systems, we take a development-centric view, where security is done best when it is done early.
Firstly, we have spent significant effort working closely with silicon partners to develop security frameworks tailored to their unique devices and technologies. So, for example, we have worked closely with NXP to support and enable the PUF technology on their latest LPC55S microcontroller family. This ensures that the latest technology is simple and easy to consume by any embedded developer. At the same time, we also support many mainstream devices, such as their K65 and K66 families, ensuring both new and existing applications can be supported.
Our Embedded Trust and C-Trust security development extensions support these devices, which IAR Embedded Workbench supports. Here through simple wizards and configuration guides, we enable developers to match their unique security profiles to a full security implementation for the device, the Security Context. We have also released Compliance Suite recently, which enables developers to take a preconfigured security context and apply it easily, instantly achieving a broad set of compliance features against the EN 303 645 requirements.
Once development is done, we enable the application to be mastered, where it is encrypted, signed, and production wrapped. This ensures that the IP is always protected against theft or malware injection. It additionally prevents overproduction, cloning, and counterfeiting, with special VPN-like tunneling to an enabled production machine anywhere in the world. This framework can provide a secure supply chain amongst multiple stakeholders in a true zero-trust environment.
John Blyler is a Design News senior editor, covering the electronics and advanced manufacturing spaces. With a BS in Engineering Physics and an MS in Electrical Engineering, he has years of hardware-software-network systems experience as an editor and engineer within the advanced manufacturing, IoT and semiconductor industries. John has co-authored books related to system engineering and electronics for IEEE, Wiley, and Elsevier.
About the Author(s)
You May Also Like





