Do you want to design a genuinely secure system? Then it’s critical to incorporate security requirements at the start of a project, i.e., at the pre-silicon verification stage.
October 14, 2021
Security is one of those requirements that tend to be an afterthought in the design process. Adding security to a system after it’s been designed leads to a compromised product. Putting it in as a critical requirement early in the design ensures a highly secure system.
Two of the most significant security issues in chip hardware design are side-channel attacks (SCA) and fault injection attacks (FIA). With SCAs, the cybercriminal measures some physical characteristics (power consumption, electromagnetic emission, etc.) when the chip performs an operation involving the secret key. Then, the attacker analyzes the acquired measurements to determine the secret key value while leaving no trace of the information being stolen.
FIAs are cheap, practical, and very dangerous attacks. Here, the attacker causes faults in chip operation (e.g., by increasing power supply voltage) and then analyzes and compares the faulty behavior with the normal behavior to determine the value of the secret key.
To learn more about the need to think about hardware security before a design architecture is completed, Design News sought out William Ruby, Chief Operating Officer (COO) at FortifyIQ, a pre-silicon security verification company. The following is a portion of that discussion.
Design News: Does DARPA have any initiatives for pre-silicon security verification?
Ruby: Yes, DARPA awarded the Automatic Implementation of Secure Silicon (AISS) program in early 2020. It’s evident that pre-silicon security verification has the attention of DARPA and the military.
Design News: Why does the protection of cryptographic keys start in hardware rather than in software?
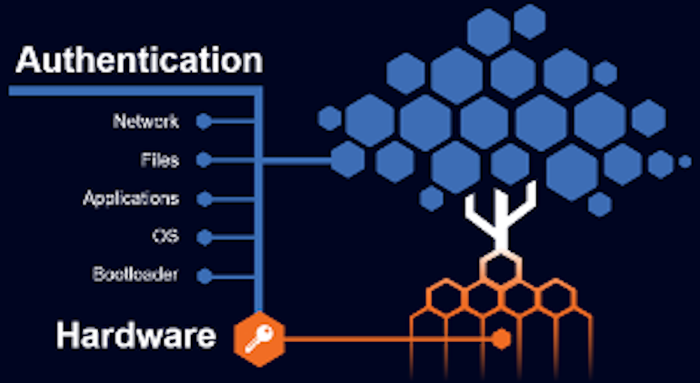
Ruby: Hardware (HW) encryption is the core, immutable foundation for all the layers of security above. Of course, not all designers see the need for HW encryption, and the upper layers of authentication are hacked/compromised on a regular basis.
Hardware vulnerabilities cannot be fixed with software or firmware. Instead, chip designers must focus on early eradication of encryption vulnerabilities before the silicon is manufactured, and certainly before the semiconductor is placed in the field with potentially disastrous impact.
Design News: How does physically unclonable function (PUF) technology fit into pre-silicon security? Or does it?
Ruby: PUF and pre-silicon security are completely different.
PUF leverages the minute physical differences in silicon. It provides a means of generating a unique key, but PUF by itself does not provide any protection from SCA/FIA. ‘Break one – break all’ no longer applies, but a single device using PUF is still susceptible to attacks. So designs using PUF must be verified using pre-silicon tools.
SideChannel Studio simulates side-channel leakage and produces simulated traces in the same formats real scopes use for traces. FaultInjection Studio simulator produces a file with the results affected by simulated faults. The simulators are software only with no dependence on physical equipment.
Design News: How can chip designers plan and implement defenses against both side-channel and fault injection attacks at the very early design stages before manufacturing?
Ruby: Use SideChannel Studio and FaultInjection Studio. Each consists of two tools – a simulator and an analyzer.
SCA vulnerabilities historically are discovered by measuring physical values such as power consumption, electromagnetic emission, etc. during chip calculations involving the secret key. The acquired measurements are analyzed to determine the secret values, i.e., the encryption key. These vulnerabilities are discovered after the chip has been manufactured, and correction mandates a redesign of the vulnerable design code and another round of manufacturing, costing significant time and money.
Fault Injection vulnerabilities are typically discovered via destructive testing of the chip, removing casings, and injecting laser signals to disrupt the behavior of the semiconductor.
With FortifyIQ Studios, after a netlist is synthesized, instead of waiting for the tape out, the netlist is used as input to the tool’s simulators, which correspond to virtual oscilloscope and fault injection equipment. Instead of real scope and a real laser connected to a real chip, which produces traces of measurements and results affected by faults, respectively, the virtual simulators connect to the chip’s netlist. SideChannel Studio simulates side-channel leakage and produces simulated traces in the same formats real scopes use for traces. FaultInjection Studio simulator produces a file with the results affected by simulated faults. The simulators are software – no physical equipment and no special skills are required.
The output of the simulators is forwarded to the analyzers for side-channel and fault injection analysis. They perform the same tests that certification labs perform, mount the same attacks that certification labs mount, and check whether there are any signs of leakage.
The SideChannel Studio analyzer will pinpoint the exact modules where the leakage occurs, corresponding to any of its parts (modules, submodules, cells of certain kinds, only combinational logic, only sequential logic, etc.)! After the source of the leakage is found, fix the RTL, synthesize it, and proceed to the next iteration of the security verification cycle – until eventually, all leakages are fixed. This is all happening while still in the pre-silicon stage.
John Blyler is a Design News senior editor, covering the electronics and advanced manufacturing spaces. With a BS in Engineering Physics and an MS in Electrical Engineering, he has years of hardware-software-network systems experience as an editor and engineer within the advanced manufacturing, IoT and semiconductor industries. John has co-authored books related to system engineering and electronics for IEEE, Wiley, and Elsevier.
About the Author(s)
You May Also Like





